Tecnologies
Webauthn
Webauthn (Web Authentication) is a web standard (W3C) specified by the FIDO Alliance that defines an interface to authenticate users to web applications and services using public key cryptography. In the client, it can be implemented in several ways: purely in software, or through a hardware gadget, such as a USB device. Also Android is certified.
The procedure has two parts:
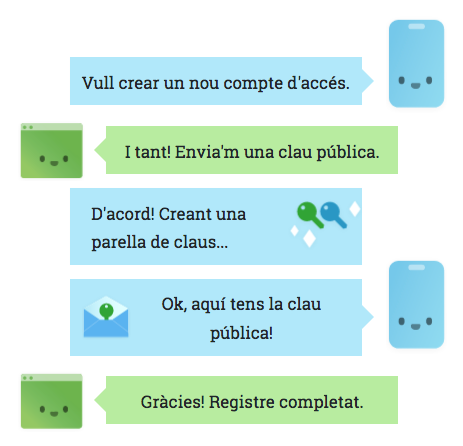
- The registration: the client sends a public key to the server, which registers it.
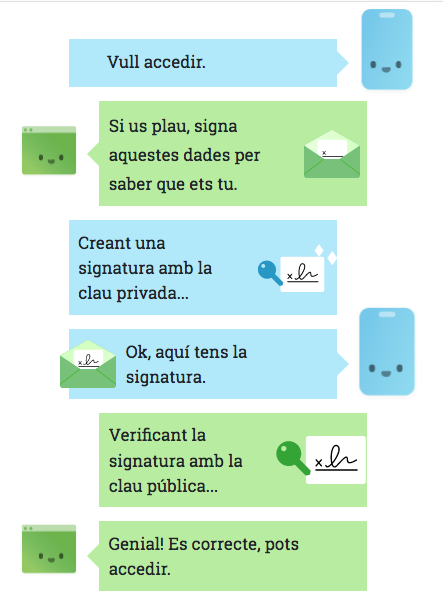
- The authentication: the server asks the client to sign some data, and verifies that it can be decrypted with the public key it has registered.
Registration of credentials
Authentication
Oauth
OAuth is a web authorization protocol for granting websites access to some of your personal data or access rights to some system.
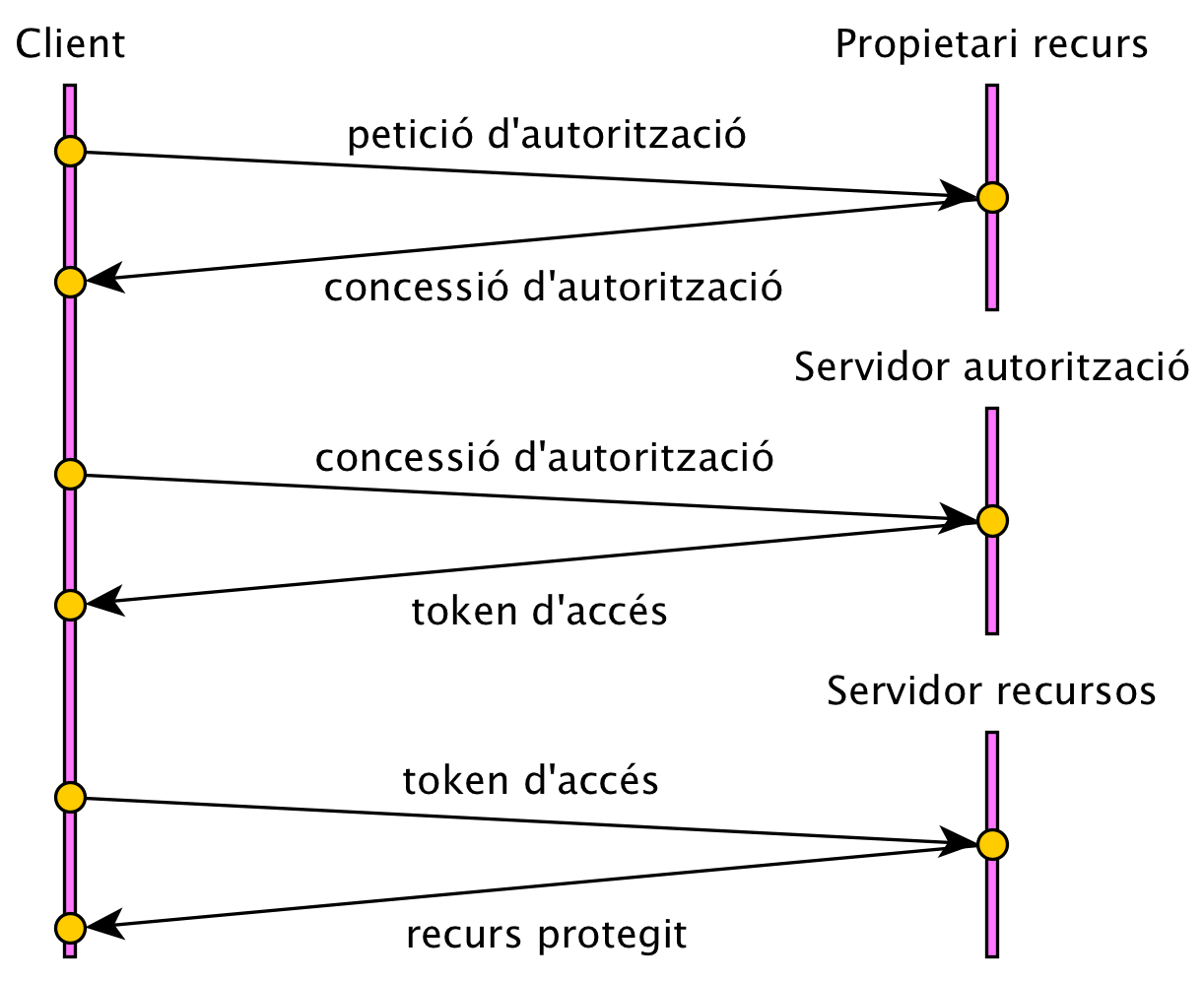
The goal is to obtain an access token to access a protected resource. There are four modes:
- Resource owner (resource owner): the user who authorizes an application to access their account.
- Client: The application that wants to access the user account.
- Resource server (resource server): contains the user accounts.
- Authorization server (authorization server): verifies identity and issues access tokens to the application.
These two servers are often referred to as the "Service API".
There are two concepts related to OAuth:
- Application registration: Before using OAuth, the application needs to register with the service by providing its name, web address and redirect URI, where the service will redirect after authorizing the 'application and where the application manages the access tokens. Registration generates a client ID and secret, used to authenticate the application to the API.
- The granting of authorization: 4 types are supported in OAuth 2:
- Authorization Code: The most common, used by server applications.
- Implicit: used by mobile or web applications (user device).
- Resource Owner Password Credentials: Used by trusted applications.
- Client Credentials: Used with Application API.
JSON Web Token (JWT)
JWT allows us to do authorization. It is an open standard based on JSON that allows the creation of access tokens to propagate identity and claims. The token is compact and can be sent in the web environment so that it can be stored on the client. The token is signed by the server (with a private key), so both the server and the client can verify that it is legitimate.
The standard statements are:
- iss: issuer
- sub: subject
- aud: audience
- exp: expiration time
- nbf: not before
- iat: issued at
- jti: JWT ID
Token-based authentication can be used to enable a stateless architecture, but it can also be used in stateful architectures. For example, a JWT can contain all necessary session data, encoded directly into the token, in which case it supports a stateless architecture. JWT can also be used to store a reference or ID for the session; in this case, the session data must be stored on the server side, making the architecture stateful.
A common operating scheme is the access token/refresh token:
- Access token: It does not go through the authentication server, it is only handled cryptographically. They don't last long (minutes).
- Refresh token: passes through the authentication server. They last longer, and can be revoked.